About ISPEC 2025
The 20th International Conference on Information Security Practice and Experience (ISPEC 2025) will be held on November 7-9, 2025 in Chengdu, organized by University of Electronic Science and Technology of China, China and IEEE Reliability Society. The ISPEC conference is an established forum that brings together researchers and practitioners to provide a confluence of new information security technologies, including their applications and their integration with IT systems in various vertical sectors. The main goal of the conference is to promote research on new information security technologies, including their applications and their integration with IT systems in various vertical sectors. Previous ISPEC has taken place in Singapore (2005), Hangzhou, China (2006), Hong Kong (2007), Sydney, Australia (2008), Xi'an, China (2009), Seoul, Korea (2010), Guangzhou, China (2011), Hangzhou, China (2012), Lanzhou, China (2013), Fuzhou, China (2014), Beijing, China (2015), Zhangjiajie, China (2016), Melbourne, Australia (2017), Tokyo, Japan (2018), Kuala Lumpur, Malaysia (2019), Nanjing, China (2021) , Taiwan (2022), Copenhagen, Denmark (2023) and Wuhan, China (2024). For all sessions, the conference proceedings were published by Springer in the Lecture Notes in Computer Science series.
Organized by:
University of Electronic Science and Technology of China, China
Organizing unit:
Nanjing University of Aeronautics and Astronautics, China
National Key Laboratory of Security Communication, China
Keynote Speakers
Note: The order of speakers is sorted according to the alphabetical order of surname.

Mohammed Atiquzzaman, Professor
Affiliation: University of Oklahoma, United
States
Bio
Mohammed Atiquzzaman obtained his M.S. and Ph.D. in
Electrical Engineering and Electronics from the University
of Manchester (UK), and BS from Bangladesh University of
Engineering and Technology. He holds the Edith Kinney
Gaylord Presidential Professorship and the Hitachi Chair
Professorship in the School of Computer Science at the
University of Oklahoma and is a life member of IEEE.
Dr. Atiquzzaman is the editor-in-chief of the Journal of
Networks and Computer Applications, founding
Editor-in-Chief of Vehicular Communications, former
co-editor-in-chief of Computer Communication, and has
served/serving on the editorial boards of many
highly-ranked journals, such as IEEE Transactions on
Mobile Computing, IEEE JSAC, IEEE Communications Magazine,
and International Journal on Wireless and Optical
Communications. He also guest-edited 12 special issues in
various journals.
He has served as symposium co-chair for many IEEE Globecom
and IEEE ICC conferences and co-chair of the IEEE High
Performance Switching and Routing Symposium. He was the
Workshop Chair of Globecom 2022 and panels co-chair of
INFOCOM'05 and is/has been on the program committee of
numerous conferences, such as INFOCOM, ICCCN, and Local
Computer Networks.
He serves on the review panels of funding agencies such as
the National Science Foundation, National Research Council
(Canada) and Australian Research Council (Australia). In
recognition of his contribution to NASA research, he
received the NASA Group Achievement Award for "outstanding
work to further NASA Glenn Research Center's effort in the
area of Advanced Communications/Air Traffic Management's
Fiber Optic Signal Distribution for Aeronautical
Communications" project. He received the IEEE 2023
Internet of Things, Ad Hoc and Sensor Networks Technical
Achievement Award for valuable contributions to the
Internet of
Things, Ad Hoc and Sensor Networks scientific community,
the IEEE 2018 Satellite and Space Communications Technical
Recognition Award for valuable contributions to the
Satellite and Space Communications scientific community,
the IEEE 2017 Distinguished Technical Achievement Award in
recognition of outstanding technical contributions and
services in the area of communications switching and
routing, and the IEEE 2020 Distinguished Service Award in
recognition of outstanding service for the benefit and
advancement of the IEEE Communications Society. Dr.
Atiquzzaman received the IEEE Fred W. Ellersick Prize for
his paper entitled "Evaluation of SCTP for Space
Networks". He has been invited to deliver keynote talks at
over 40 international conferences around the globe,
including USA, Brazil, Italy, Poland, Portugal, Australia,
China, Taiwan, Malaysia, and Korea.
His research interests include satellite communications,
wireless and mobile networks, vehicular networks, ad hoc
networks, Quality of Service, and optical communications.
His research has been funded by the National Science
Foundation (NSF), National Aeronautics and Space
Administration (NASA), U.S. Air Force, Cisco, Honeywell,
Oklahoma Department of Transportation, and Oklahoma
Highway Safety Office. He has over 450 refereed technical
publications, many of which can be accessed at
www.cs.ou.edu/~atiq.

Shui Yu, Professor
Affiliation: University of Technology Sydney,
Australia
Bio
Shui Yu is Professor of the School of Computer Science in
the Faculty of Engineering and Information Technology at
UTS, the Deputy Chair of the UTS Research Committee, and
is a researcher of cybersecurity, privacy and the
networking, communication aspects of Big Data, and applied
mathematics for computer science.
In 2013, he initiated a new field, networking for big
data, in the networking and communication domain. Shui was
the leading editor of Networking for Big Data, published
in 2015, which supplied an unprecedented look at
cutting-edge research on the networking and communication
aspects of Big Data.
Many of his research outputs have been adopted by
industry, for example, the auto scale strategy of Amazon
Cloud against distributed denial-of-service attacks.
As the corporate world has increasingly adopted new
technologies to analyze and store vast amounts of data in
a bid to generate valuable insights and unlock strategic
value, Shui has concentrated on the privacy and security
concerns associated with big data.
Among other issues, he has researched security issues
associated with smart grids, which present opportunities
to help solve the problems of carbon emissions and the
energy crisis.
He has also investigated creating anonymous transactions
on Blockchain to deal with threats to users' privacy. His
anonymous communication work for web browsing privacy has
been cited by more than 200 US patents.
He has published two monographs and edited two books, and
produced more than 600 technical papers, published in top
journals such as IEEE TPDS, TC, TIFS, TMC, TKDE, TETC,
ToN, and INFOCOM. His h-index is 80.
Shui serves his research communities in various roles,
including serving on the editorial boards of IEEE
Communications Surveys and Tutorials, IEEE Communications
Magazine and the IEEE Internet of Things Journal, among
others.
He has been a member of organizing committees for many
international conferences, such as the publication chair
for IEEE Globecom 2015, IEEE INFOCOM 2016 and 2017, TPC
chair for IEEE Big Data Service 2015, and general chair
for ACSW 2017.
He served as a Distinguished Lecturer of IEEE
Communications Society (2018-2021). He is a Distinguished
Visitor of IEEE Computer Society (2022-2024), a voting
member of IEEE ComSoc Educational Services board, and an
elected member of Board of Governors of IEEE
Communications Society and IEEE Vehicular Technology
Society, respectively. He is a Fellow of IEEE.
Call For Papers
Authors are invited to submit full papers presenting new research results related to information security technologies and applications. Areas of interest include, but are not limited to:
- Cryptology
- Applied cryptography
- Mobile security
- Cloud security
- Access control
- Privacy enhanced technology
- Viruses and malware
- Software security
- Database security
- Web security
- Operating system security
- Intrusion detection
- Big data security and privacy
- Biometric Security
- Implementation
- Network security
- Key management
- Security and privacy in ubiquitous computing
- Formal methods for security
- Digital forensics
- Security for critical infrastructures
- Embedded systems security
- Lightweight security
- Smart grid security
- Cyber security for urban transportation
- Cyber-physical security
- Cryptocurrency
Publication Information
The conference proceedings will be published by Springer in the Lecture Notes in Computer Science (LNCS) series. Previous ISPEC proceedings are available on SpringerLink, where you can find detailed metrics including citations, downloads, and reader statistics at both paper and book levels.
Paper Preparation Guidelines
Authors must prepare their papers using either the LaTeX or Word templates provided by Springer. Please consult Springer's Instructions for Authors of Proceedings for detailed formatting guidelines.
Code of Conduct
All authors are required to adhere to Springer Nature's Code of Conduct for book authors.
Important Dates
| Important Dates | ||
|---|---|---|
| First Round | Paper Submission | July 7, 2025 |
| Acceptance Notification | July 31, 2025 | |
| Camera-ready Version | August 15, 2025 | |
| Second Round | Paper submission | August 15, 2025 |
| Acceptance Notification | To be Announced | |
| Camera-ready Version | To be Announced | |
Author Instructions
Authors are invited to submit original papers: they must not substantially duplicate work that any of the authors have published elsewhere or have submitted in parallel to any other conferences that have proceedings or any journal. The submission must be anonymous, with no author names, affiliations, acknowledgements, or obvious references. Original contributions are invited up to 16 pages in length (single column) excluding appendices and bibliography and up to 20 pages in total, using at least 11-point fonts and with reasonable margins. Submissions not meeting the submission guidelines risk rejection without consideration of their merits.
Organising Committee
Honorary Co-Chairs
Robert H. Deng, Singapore Management University,
Singapore
Zhiguang Qin, University of Electronic Science and
Technology of China, China
General Co-Chairs
Zhen Qin, University of Electronic Science and Technology of
China, China
Kuo-Hui Yeh, National Yang Ming Chiao Tung University,
Taiwan
Abderrahim Benslimane, University of Avignon, France
Technical Program Co-Chairs
Hu Xiong, University of Electronic Science and Technology of
China, China
Mohammed Atiquzzaman, University of Oklahoma, United
States
Lu Zhou, Nanjing University of Aeronautics and Astronautics,
China
Panel Co-Chairs
Xuyun Nie, University of Electronic Science and Technology
of China, China
Zhe Liu, Zhejiang Lab, China
Liming Fang, Zhejiang, China
Poster Co-Chairs
Jun Shao, Zhejiang Gongshang University, China
Local Arrangement Co-Chairs
Chaosheng Feng, Sichuan Normal University, China Rong Wang,
Sichuan Normal University, China
Yuan Yuan, Sichuan Normal University, China
Hongjie Zhang, Sichuan Normal University, China
Chu Chu, Sichuan Normal University, China
Weixi Zhou, Sichuan Normal University, China
Publication Chair
Erqiang Zhou, University of Electronic Science and
Technology of China, China
Zengpeng Li, Shandong University, China
Xiaogang Xu, Huawei 2012 Labs, China
Publicity Co-Chairs
Fuhu Deng, University of Electronic Science and Technology
of China, China
Weizhi Meng, Lancaster University, United Kingdom
Chunhua Su, University of Aizu, Japan
Han-Chieh Chao, Fo Guang University, Taiwan
Yong Xiang, Deakin University, Australia
Yingjiu Li, University of Oregon, US
Zhen Ling, Southeast University, China
Chunpeng Ge, Shandong University, China
Special Session Co-Chair
Weizheng Wang, City University of Hong Kong, Hong Kong
Chien-Ming Chen, Nanjing University of Information Science
and Technology, China
Web Chair
Ye Xia, Univesity of Electronic Science and Technology of
China, China
Zengxiang Wang, Univesity of Electronic Science and Technology of
China, China
Jiafei Wu, University of Aizu, Japan
Execution Co-Chair
Dequan Xu, Guizhou University, China
Tsu-Yang Wu, Nanjing University of Information Science and
Technology, China
Conference Committee Chair
Bingjie XU
Program Committee Chair
Bo Tian
Session Track Chair
Yue Zhao
Special Issues
As part of the publication plan, ISPEC 2025 will apply for discounted article processing charges (APCs) for extended versions of selected manuscripts recommended to Special Issues in open access journals.
- AI Security and Safety in Computational Social Systems, IEEE Transaction on Computational Social Systems.
- Selected Papers: The 20th International Conference on Information Security Practice and Experience (ISPEC 2025), Symmetry.
- Challenges and Solutions in Large Language Models, Joint Journals.
- Emerging Technologies with Symmetry for Zero Trust, Symmetry.
- Information and Future Internet Security, Trust and Privacy—3rd Edition, Future Internet.
- Advanced Vehicular Ad Hoc Networks: 2nd Edition, Sensors.
- Recent Advances in Data Privacy, Transparency and Cybersecurity: Theory and Applications, Applied Science.
- Heuristic Algorithms for Optimizing Network Technologies: Innovations and Applications, Computers, Materials & Continua.
- Security, Safety, and Ethics of AI-Driven Innovations for Digital Health, Digital Health (SCIE/SSCI).
Accepted Papers
2025 Full paper
1 Secure Aggregation Scheme for Federated Learning with Bilateral Verification in the Internet of Vehicles
2 Research on image-based vulnerability detection of embedded firmware
3 Adversarial Defense via Clean-Sample Guided Adaptive Overlapping Patch for Traffic Sign Recognition Systems
4 Zero-recollecting Mobile-app Identification over Drifted Encrypted Network Traffic
5 Efficient AES Side-Channel Attacks Based on Residual Mamba Enhanced CNN
6 Research on Video Steganography Based on Optical Flow Perception and Discrete Wavelet Transform
7 Publicly Verifiable Multi-server Homomorphic Secret Sharing
8 APersonalized Federated Matrix Decomposition Recommendation Algorithm Based on Meta-Distillation
9 NIDS-GPT :A new GPT-based model for anomaly data package detection
10 Critical Neuron-Based Backdoor Defense for Federated Learning: A Combined Dropout and Local Outlier Factor Approach
12 Self-Supervised CNN for Video Double Compression Detection via Artifact Prediction
13 Authenticated and Incremental Single-Server Private Information Retrieval
14 Meet-in-the-Middle Preimage Attacks with Multi-Match on ASCON-XOF
16 Mixderive A New Framework of Deriving Linear Approximations and Improved Differential-Linear Distinguishers for ChaChal
17 An RPKI Certificate Validator for Formal Correctness
18 A New Cryptanalytic Technique on Bit-Oriented Stream Ciphers and Application to ACORN v314 Meet-in-the-Middle Preimage Attacks with Multi-Match on ASCON-XOF
19 A novel S-box construction technique based on the improved genetic algo-rithms through 2N-round searching.
20 A Fully Anonymous Authentication Scheme with Cryptographic Reverse Firewalls in Vehicle-to-Grid Networks
22 Towards a Lattice-Based Non-Interactive Aggregate Signature Scheme Following the Fiat-Shamir with Aborts Paradigml
ISPEC's past papers
Best Paper
Awaiting evaluation
Registration Information
-
The early registration deadline is 16 October 2025. All authors must register before this date. Other attendees should try to complete registration before this date.
-
Registration for the conference cannot be canceled. There is no refund of registration fees.
-
Contact 1841974993@qq.com with subject "ISPEC Registration" if you have any registration problem.
Registration
| Type | Price |
|---|---|
| Author Registration | 4000CNY/600USD |
| Standard (Before 16 October) | 4000CNY/600USD |
| Standard (Starting 17 October) | 4500CNY/650USD |
How to Register
Fill out the registration form for foreign attendees or registration form for attendees from Mainland China with all required details and email the filled form to 1841974993@qq.com with the subject of your email " ISPEC 2025 Registration for #PAPER-ID(if applicable)#NAME" (where PAPER-ID is the submission number of your paper and NAME is the author name). In the email please include 1) a copy of the bank draft or bank wire receipt or Transaction ID of your registration fee payment, 2) Name of the author who will give presentation during the conference.
International Payment:
PAYMENT BY PAYPAL In USD(Please Wait)
For Chinese Residents:
开户银行名称:中国工商银行股份有限公司成都昭觉南路支行
帐号:4402 0019 0910 0166 270
户名:四川启明鑫旅游服务有限公司
汇款备注信息:"ISPEC#论文编号(如适用)#姓名"
Overseas participants should check if they need to apply for a Chinese visa.
In 2025, China has expanded its visa-free access to additional countries. Building on last year's inclusion of France, Germany, Italy, the Netherlands, Spain, and Malaysia, the list now also includes Switzerland, Ireland, Hungary, Austria, Belgium, Luxembourg, New Zealand, Australia, and Poland.
Moreover, citizens of the following 54 countries and regions can enjoy a 144-hour visa-free transit policy when visiting Chengdu(via Tianhe Airport): Austria, Belgium, Czech Republic, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Iceland, Italy, Latvia, Lithuania, Luxembourg, Malta, the Netherlands, Poland, Portugal, Slovakia, Slovenia, Spain, Sweden, Switzerland, Monaco, Russia, the United Kingdom, Ireland, Cyprus, Bulgaria, Romania, Ukraine, Serbia, Croatia, Albania, Belarus, Norway, the United States, Canada, Brazil, Mexico, Argentina, Chile, Australia, New Zealand, South Korea, Japan, Singapore, Brunei, the United Arab Emirates, and Qatar.
To the best of our knowledge, to enjoy the 144-hour visa-free transit policy: 1) the passport must have a minimum validity of 3 months; 2) no previous record of being denied a Chinese visa; 3) the departure location before arriving in Chengdu and the destination after leaving Chengdu must be in different countries or regions (e.g. from Tokyo to Chengdu and from Chengdu to Hong Kong).
Important: the above information only indicates that you may not need a Visa to visit Chengdu, but please double check the Visa policy from an official source before making your travel arrangement!
If you need an invitation letter to support your visa application, please contact the Local Arrangement Co-Chair Dr.Chaosheng Feng(email: csfenggy@sicnu.edu.cn)
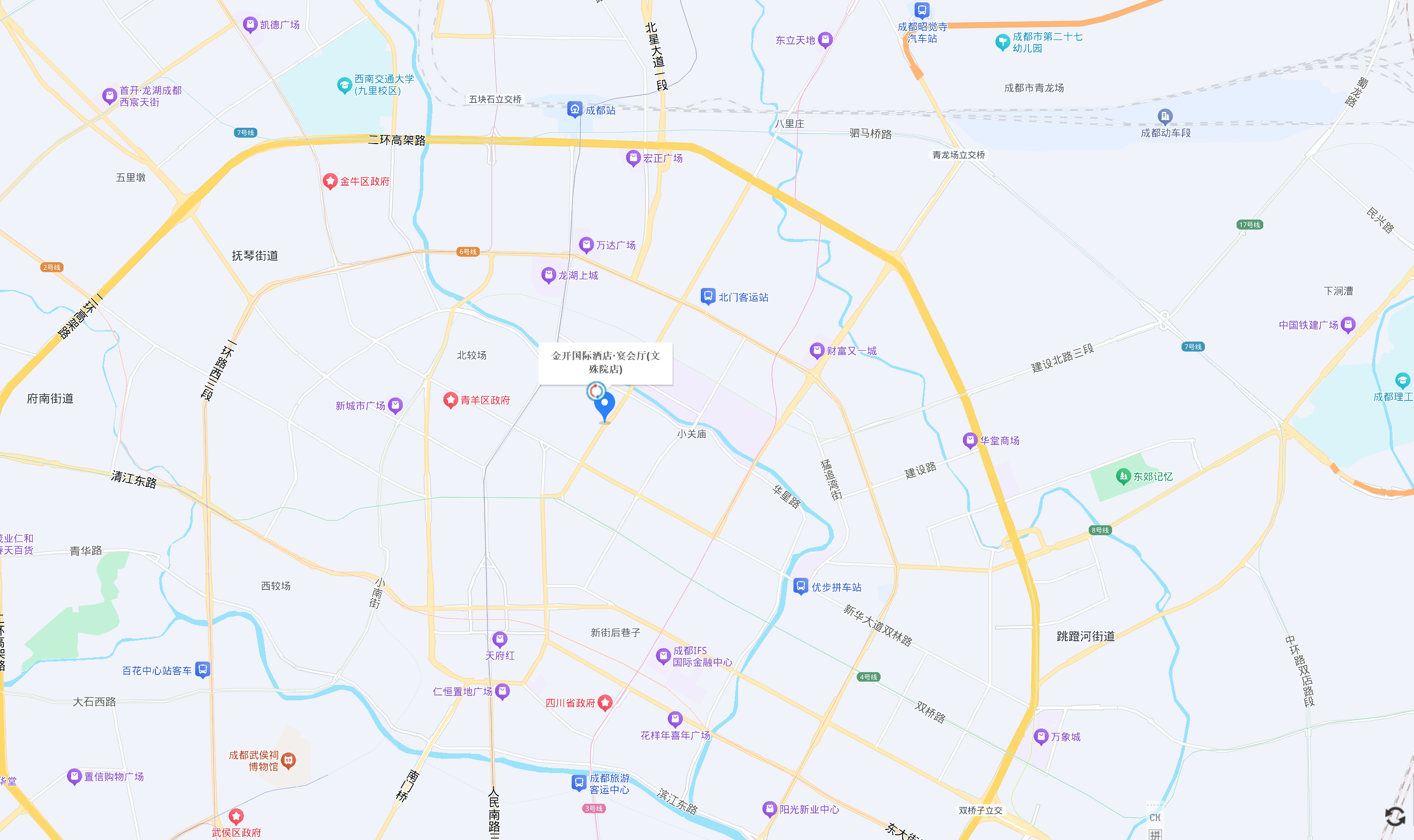
Important: if you need a room during the conference, please contact the local organization team via Email: 1841974993@qq.com. We have secured a number of rooms for the attendances who have registered.
Hotel Name:
Jinkai International Convention Center (金开国际会议酒店)
Address:
No. 2 North Street, Caoshijie Street, Qingyang District, Chengdu (next to Wenshu Monastery) (成都市青羊区草市街街道北大街2号(文殊坊旁))
Hotel Description:
Jinkai International Convention Center is a high-end business and conference hotel located in the heart of Chengdu’s Qingyang District, adjacent to the renowned Wenshu Monastery and surrounded by rich cultural heritage. The hotel integrates accommodation, dining, and conference facilities, making it an ideal venue for business meetings, exhibitions, and leisure travel.
The hotel offers spacious and elegantly designed guest rooms equipped with modern amenities, ensuring guests enjoy both comfort and convenience. Its state-of-the-art convention halls are suitable for large-scale conferences and banquets, supported by professional event services.
How to Reach:
- From Chengdu Shuangliu International Airport: you can take a taxi (about 40 CNY, 40–50 min), or take Metro Line 19 at Taipingyuan Station(太平园站), transfer to Line 17 at Jiujiang North Station(九江北站), and get off at Chenghuang Tample Station (城隍庙站); from there, it’s about a 13-minute walk to the hotel (around 8 CNY, 60 min total).
- From Chengdu East Railway Station: you can take a taxi (about 30 CNY, 30 min), or take Metro Line 2 at Chengdu East Railway Station(成都东客站), transfer to Line 1 at Tianfu Square Station(天府广场站), and get off at Wenshu Monastery Station (文殊院站), then walk about 14 minutes to the hotel (around 6 CNY, 45 min total).
- From Chengdu Tianfu International Airport: you can take a taxi (about 100 CNY, 70-90 min), or take Metro Line 18 at Tianfu International Airport Station(天府国际机场站), transfer to Line 1 at South Railway Station(火车南站), and get off at Wenshu Monastery Station (文殊院站); from there, it’s about a 14-minute walk to the hotel (around 8 CNY, 90 min total).
Hotel Map:
Hotel Pictures:

Conference Schedule
| Date | Time | Content |
|---|---|---|
| Nov 7, 2025 Day 1 |
15:00 - 20:00 | Conference Registration |
| 18:00 - 20:00 | Welcome Dinner | |
| Nov 8, 2025 Day 2 |
08:30 - 09:00 | Opening Ceremony |
| 09:00 - 09:30 | Keynote Talk 1 Keynote Chair: Prof. Lu Zhou, Nanjing University of Aeronautics and Astronautics, China Title: Secure Car-to-car Communication-enabled Internet of Vehicles Speaker: Prof. Mohammed Atiquzzaman |
|
| 09:30 – 10:00 | Keynote Talk 2 Keynote Chair: Prof. Lu Zhou, Nanjing University of Aeronautics and Astronautics, China Title: Security for Industrial Automation and Control Systems - Integrated with the IEC 62443 Standard Speaker: Prof. Kuo-Hui Yeh |
|
| 10:00 - 10:15 | Coffee Break | |
| 10:15 – 10:45 | Keynote Talk 3 Keynote Chair: Prof. Kuo-Hui Yeh, National Dong Hwa University, Hualien Title: Security Challenges and Exploration for In-Vehicle Multimodal Large Models Speaker: Prof. Lu Zhou |
|
| Session 1: Federated Learning (5 talks) Session Chair: Prof. Lu Zhou, Nanjing University of Aeronautics and Astronautics, China |
||
| 10:45 - 11:00 | [1] Secure Aggregation Scheme for Federated Learning with Bilateral Verification in the Internet of Vehicles Yinghui Zhang, Mengxi Wang, Yangguang Tian | |
| 11:00 - 11:15 | [8] Personalized Federated Matrix Decomposition Recommendation Algorithm Based on Meta-Distillation Xianwei Yin, Tao Zhang, Jangkai Gao, Hongjie Zhang, Rong Wang, Chaosheng Feng | |
| 11:15 - 11:30 | [10] Critical Neuron-Based Backdoor Defense for Federated Learning Ding Chen, Xu Chen, Zuli Wang, Juan Wang, Lei Shi, Yimin Zhou | |
| 11:30 - 11:45 | [26] Free-Rider Detection Mechanism for Federated Learning-Based Intrusion Detection System Son Ngo Duc Hoang, Nguyen Tran Duc An, Truong Tuan Phi, Nguyen Thi Thu, Hien Do Hoang, Nghia To, Van-Hau Pham | |
| 11:45 - 12:00 | [32] Reputation-Based Dynamic Aggregation Node Selection Method for Federated Learning Kaifa Zheng, Yiming Hei, Chenling Bai, Zhen Xu, Jun Wang, Lei Li, Tiejun Wu, Jiayi Liu, Di Zhou | |
| 12:00 - 14:00 | Lunch | |
| Session 2: Cryptography and Security Protocols (7 talks) Session Chair: Prof. Lu Zhou, Nanjing University of Aeronautics and Astronautics, China |
||
| 14:00 - 14:15 | [7] Publicly Verifiable Multi-server Homomorphic Secret Sharing Ye Xu, Takashi Nishide | |
| 14:15 - 14:30 | [14] Meet-in-the-Middle Preimage Attacks on ASCON-XOF Shun Zhang, Tairong Shi, Jie Guan, Mingyao Gao, Ziyu Guan | |
| 14:30 - 14:45 | [16] Mixderive: A New Framework for Linear Approximations and Differential-Linear Distinguishers for ChaCha Zhengting Li, Lin Ding, Xinhai Wang, Jiang Wan, Honglei Wang | |
| 14:45 - 15:00 | [18] A New Cryptanalytic Technique on Bit-Oriented Stream Ciphers: Application to ACORN v3 Xinhai Wang, Lin Ding, Jiang Wan, Zhengting Li | |
| 15:00 - 15:15 | [19] Novel S-box Construction Based on Improved Genetic Algorithms Runlian Zhang, Zhaowen Huang, Xiaonian Wu, Hailong Zhang, Lingchen Li | |
| 15:15 - 15:30 | [22] Lattice-Based Non-Interactive Aggregate Signature Following the Fiat-Shamir with Aborts Paradigm Mingmei Zheng, Masahiro Mambo, Junzuo Lai, Xinyi Huang | |
| 15:30 - 15:45 | [23] Distributed Key Generation for SM2 and Its Applications to Threshold Encryption Boxun Li, Zhiyuan An, Yantao Zhong, Jing Pan | |
| 15:45 - 16:00 | Coffee Break | |
| Session 3: Cybersecurity and Intrusion Detection (6 talks) Session Chair: Prof. Lu Zhou, Nanjing University of Aeronautics and Astronautics, China |
||
| 16:00 - 16:15 | [4] Zero-recollecting Mobile-app Identification over Drifted Encrypted Network Traffic Minghao Jiang, Kejiang Ye, Wei Cai, Xu Zhou | |
| 16:15 - 16:30 | [17] An RPKI Certificate Validator for Formal Correctness Yajun Teng, Wei Wang, Jingqiang Lin, Shijie Jia, Xiaoqi Jia | |
| 16:30 - 16:45 | [27] G-FLEX: Graph-based Transformer Framework for Fileless Malware Detection Bao Pham-Thai, Khoa Nghi Hoang, Son Ngo Duc Hoang, Khanh Ho-Vi, Duy Phan | |
| 16:45 - 17:00 | [28] Blockchain-Based Real Estate Contract Authentication System for the Ejar Platform Abubaker Wahaballa, Rawabi Alshehaywin, Leena Aloraini, Layan Almubarak, Mohammed A.O. Alsayed | |
| 17:00 - 17:15 | [30] Traceable Multi-signature Scheme with Distributed Combiners for Accountable Blockchain Transactions Jingrui Wang, Jun Zhou, Zhenfu Cao, Xiaolei Dong | |
| 17:15 - 17:30 | [33] APT Attack Detection with Heterogeneous Provenance Graphs Phan The Duy, Dinh Minh Thien, Truong Thi Hoang Hao, Khoa Ngo-Khanh, Van-Hau Pham | |
| 17:30 - 20:00 | Banquet | |
| Nov 9, 2025 Day 3 |
09:00 - 09:40 | Keynote Talk 4 Chair: Prof. Kuo-Hui Yeh, National Dong Hwa University, Hualien Title: Artificial Intelligence for Network Security: Today and Tomorrow Speaker: Prof. Shui Yu |
| 09:40 - 10:20 | Keynote Talk 5 Chair: Prof. Kuo-Hui Yeh, National Dong Hwa University, Hualien Title: Enhancing Robustness in Deep Learning: A Universal Mechanism for Adversarial Example Detection Speaker: Prof. Han-Chieh Chao |
|
| 10:20 - 11:00 | Keynote Talk 6 Chair: Prof. Kuo-Hui Yeh, National Dong Hwa University, Hualien Title: Blockchain Data Analysis: Privacy Preservation with Regulation Speaker: Prof. Weili Han |
|
| 11:00 - 11:20 | Coffee Break | |
| Session 4: Multimedia Security and Side-Channel Attacks (3 talks) Session Chair: Prof. Kuo-Hui Yeh, National Dong Hwa University, Hualien |
||
| 11:20 - 11:35 | [2] Image-based Vulnerability Detection of Embedded Firmware Juan Wang, Yuheng Zeng, Shuchen Qin, Nihong Zhu, Yimin Zhou, Yu Zhang | |
| 11:35 - 11:50 | [6] Video Steganography Based on Optical Flow Perception and Discrete Wavelet Transform Wei Wang, Jie Luo, Juan Wang, Yimin Zhou | |
| 11:50 - 12:05 | [12] Self-Supervised CNN for Video Double Compression Detection via Artifact Prediction Rui Zhang | |
| 12:05 - 14:00 | Lunch | |
| Session 5: Privacy Protection and AI Security (6 talks) Session Chair: Prof. Yue Zhao, National Key Laboratory of Security Communication, China |
||
| 14:00 - 14:15 | [3] Adversarial Defense via Clean-Sample Guided Adaptive Overlapping Patch Juan Wang, Shuchen Qin, Yang Chen, Yuheng Zeng, Nihong, Yimin Zhou, Yu Zhang | |
| 14:15 - 14:30 | [9] NIDS-GPT: A GPT-based Model for Anomaly Packet Detection Zuli Wang, Qianchi Yang, Chunyu Wang, Yimin Zhou, Yu Zhang | |
| 14:30 - 14:45 | [13] Authenticated and Incremental Single-Server Private Information Retrieval Pengfei Lu, Zengpeng Li, Mei Wang | |
| 14:45 - 15:00 | [20] Fully Anonymous Authentication with Cryptographic Reverse Firewalls in Vehicle-to-Grid Networks Jingxue Chen, Juhao Wang, Yiming Chen, Yining Liu, Jingcheng Song | |
| 15:00 - 15:15 | [24] Enhancing FIDO2 Authentication Security via Markov Decision Process-based Risk Assessment Yu Jen Wang, Kuo-Hui Yeh, Taif Khalifah Alghufaily | |
| 15:15 - 15:30 | [31] Assessing the Security of Vibe Coding: Baseline vs Security-Oriented Prompts in LLM Code Generation Runtong He, Huishan Lai, Jingxue Chen, Chunhua Su | |
| 15:30 - 15:45 | Closing Ceremony & Banquet | |





